
Feature – Privacy across the enterprise
My Role – Planning – UX Design – UI Design – UX Research
Problem statement
In 2018, the European Union passed the General Data Protection Regulation (GDPR). It is a very large and sweeping law regarding privacy of user data. Any company wishing to operate in the European markets would have to comply.
Atlassian is a world leader in collaborative productivity software, which presented a number of unique challenges in regards to protecting personal information of users. I was responsible for addressing this through research and design for our enterprise customers.
Problems with privacy
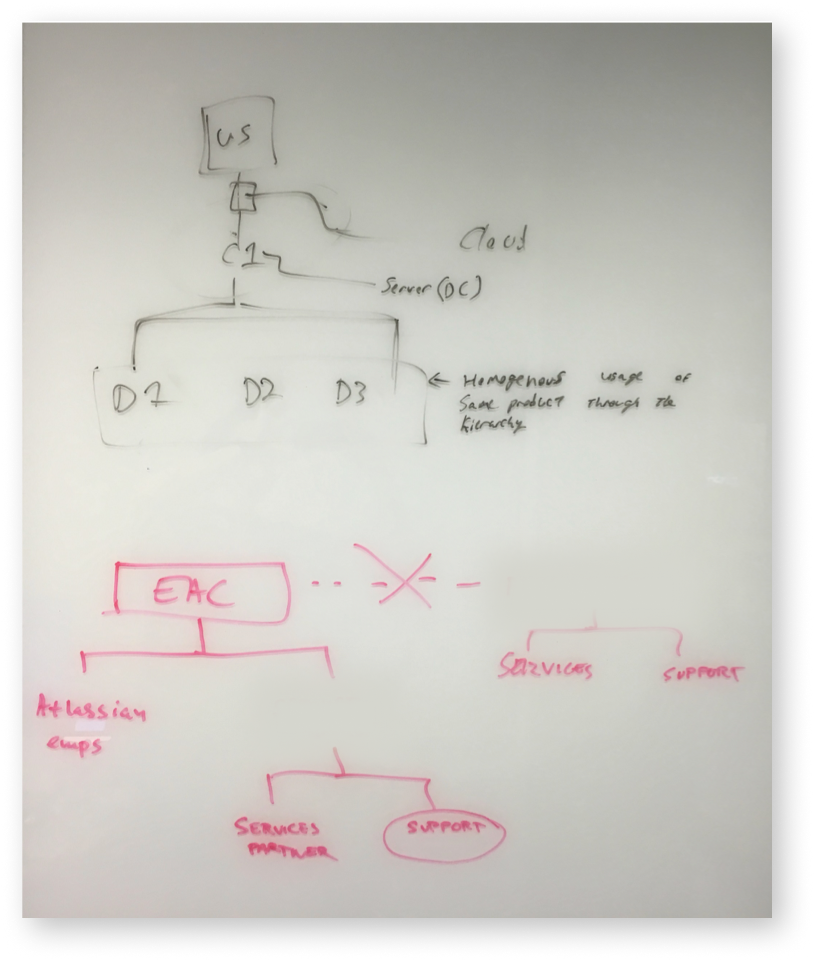
The Technical Account Managers (TAM) knew the most about this, each handles four enterprise accounts personally and was a conduit of direct feedback from users.
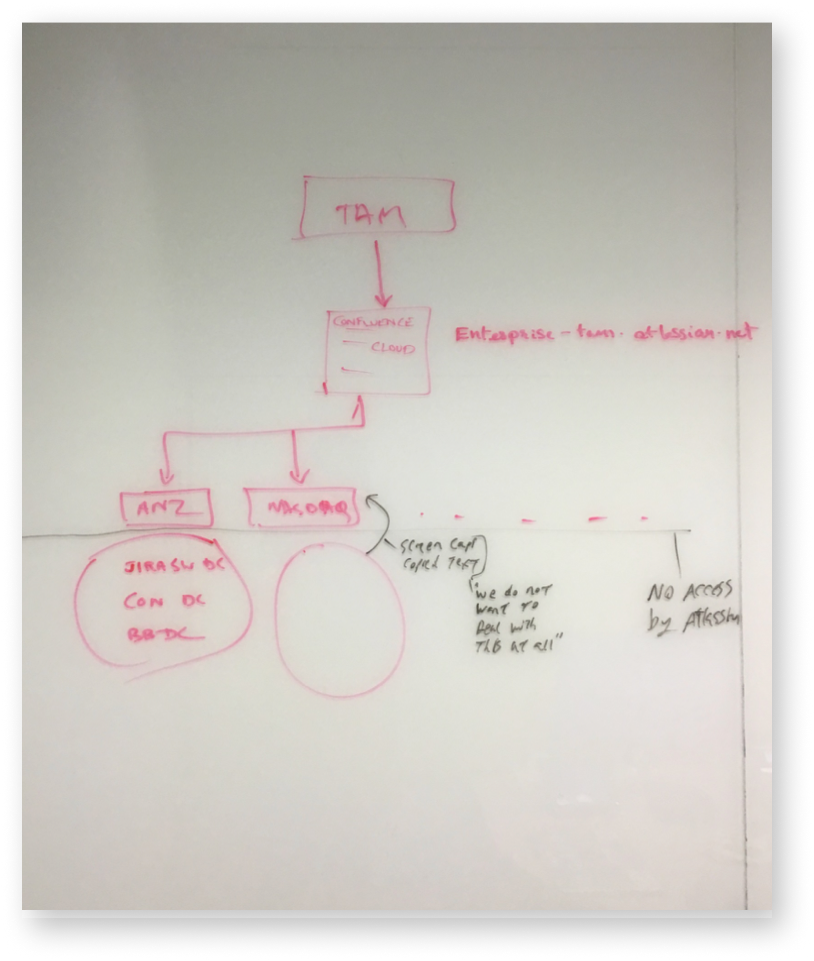
We wanted to identify problems and form hypothesis, then bring them to customers for validation. Then we would be able to make a journey map to plot out pain points and ideas for solutions.
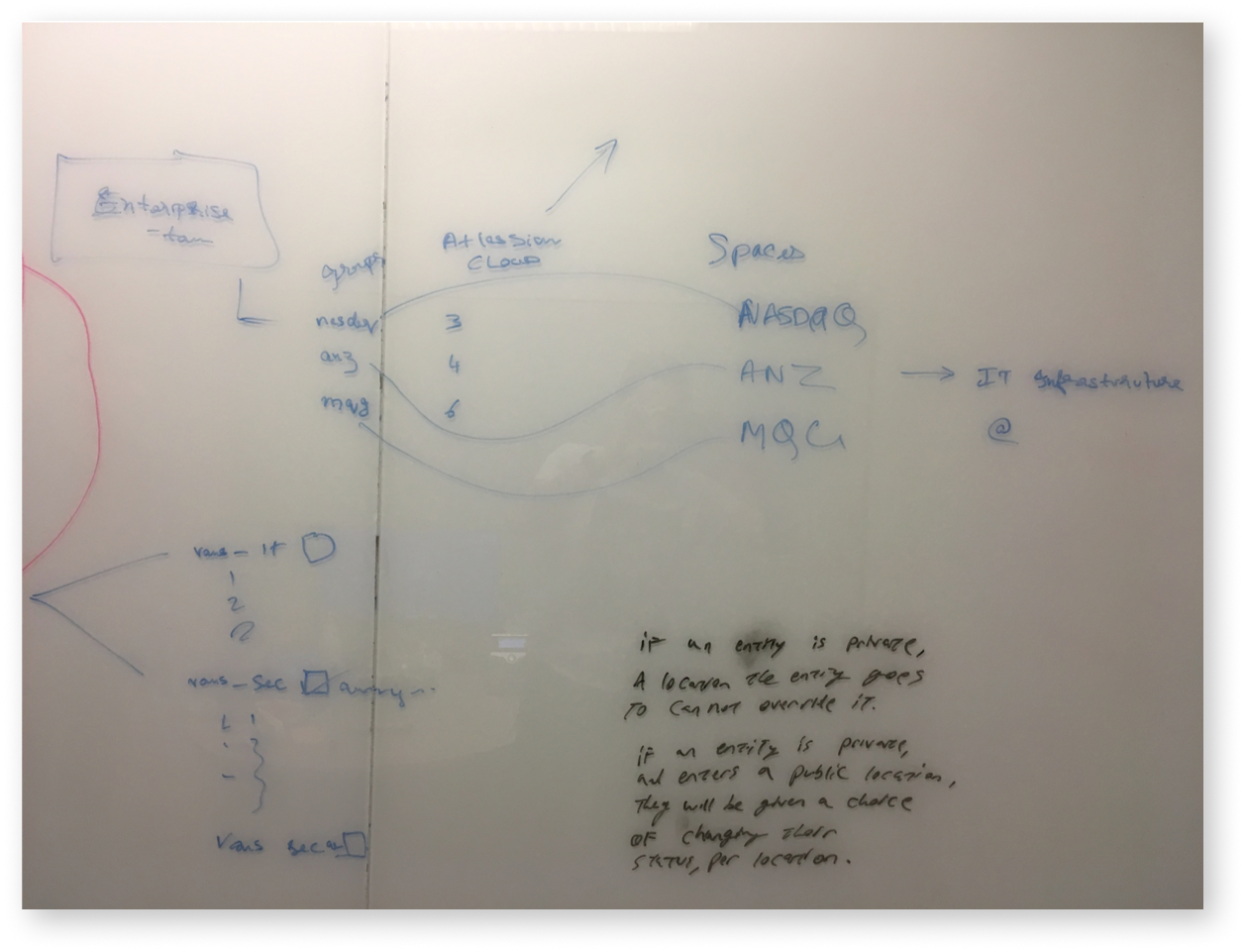
In this case, the TAM operated as a facilitator or mediator. If a user has an issue, a TAM can ask around to see if other users have the same issue or have an answer, connecting people together to problem solve.
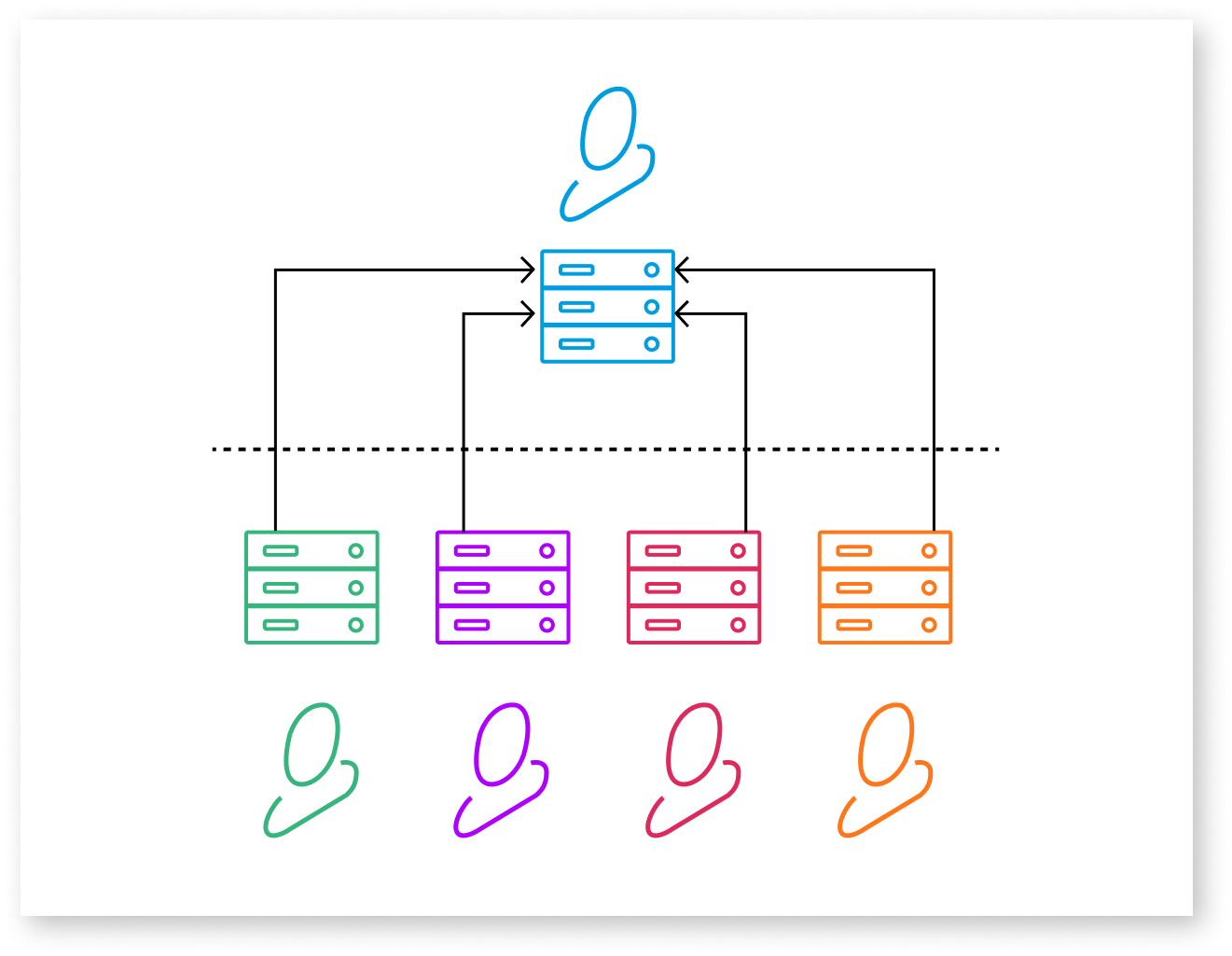
Working together in a group environment, even a secure system, had the side effect of exposing the identity of the users.
What is an alias?
In Atlassian products, an alias is the name used to identify a specific user. This identity shows up next to everything a user does across all Atlassian products. Atlassian feature teams work in a triad model made up of a feature owner, the lead developer, and a senior designer. Working with my triad, we mapped out how a user moves thorough the system.
When Atlassian products are connected together, that name can move freely between products. If a user has contributed to a document in anyway then their identity moves with the document. This meant that currently users were unaware of where their identity went.
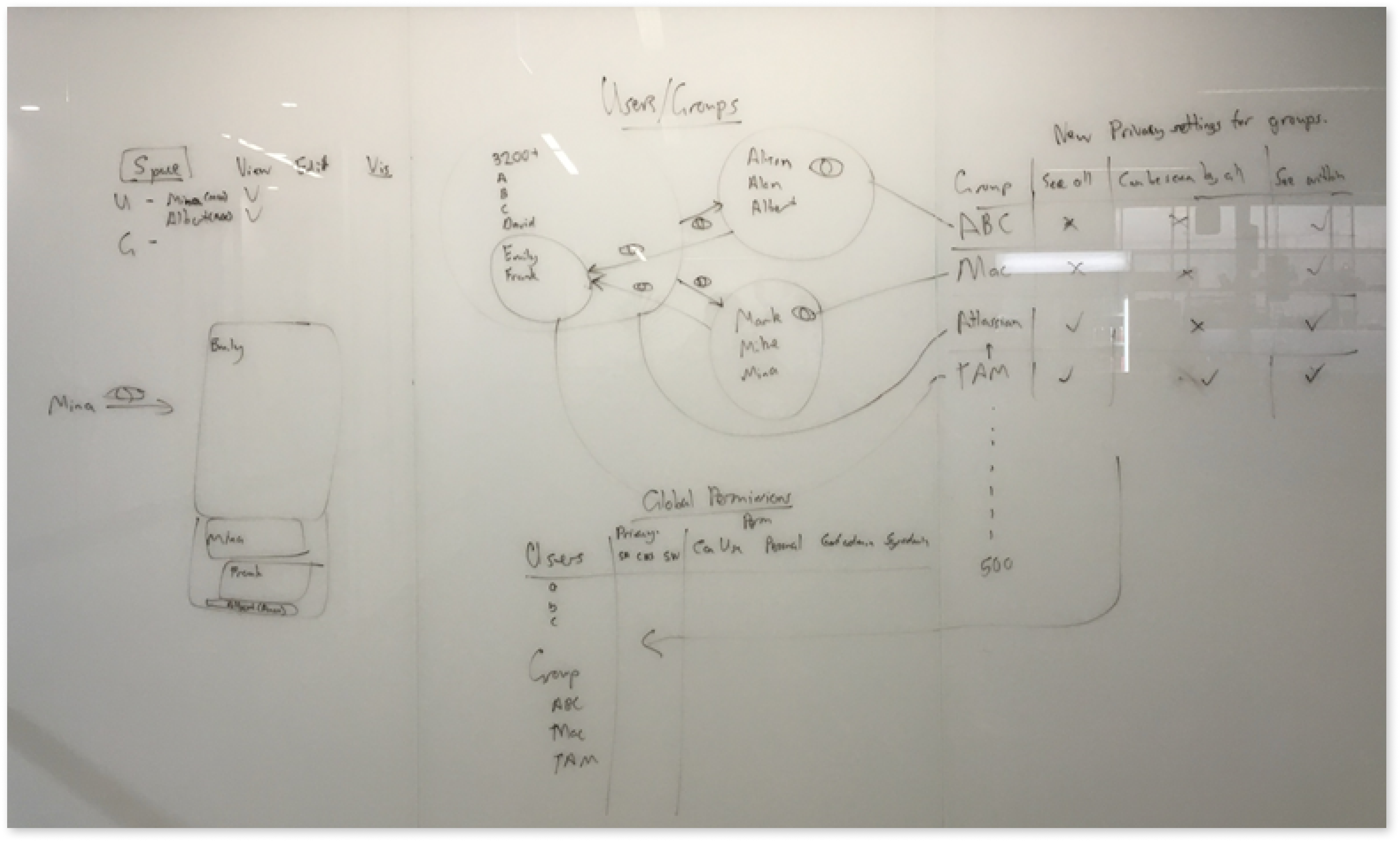
Exposure of identity
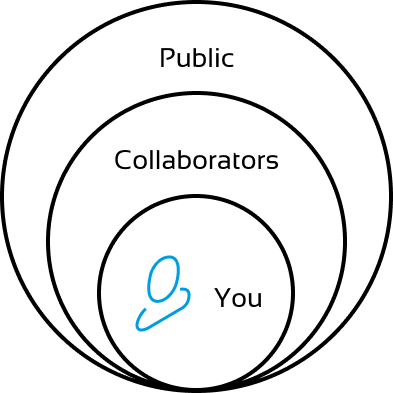
At the core level, all aspects of your can be available to anyone. This is your photo, email, contact info, and the ability to follow through a system. At the next level up, your photo is available as is email, but following is limited to collaborators you give permission to.
At the final level, you are fully anonymous. There is no way to know your identity or follow you. In this example, this is a simulated identity.





Learning about huge collaborative systems
I learned that it is possible for a system to get so large that very few people understand how it all works. When this happens, experiences become fragmented across such a huge product.
Having an overall story of what users want to get out of using a product provides a framework for organizing these kinds of features. In this case, it is a framework of privacy experiences.
Doing this work after the fact, as it grows into a product organically, can be time consuming and difficult as you chase down all the ways exposure can occur.
